In an age where data is the lifeblood of our digital existence, ensuring its security has become paramount. Two commonly employed methods in this regard are Encryption and Data Tokenization. While both serve the purpose of safeguarding information, they do so in different ways and have distinct advantages and disadvantages. This article delves into the world of Encryption and Data Tokenization, shedding light on their workings, differences, and the best scenarios for their application.
Table of Contents
How Encryption Works
Principles of Encryption
Encryption is the process of converting plain text into an unintelligible form, known as ciphertext, using complex mathematical algorithms. The fundamental principle behind encryption is to protect sensitive data by making it unreadable to unauthorized parties. Encryption relies on cryptographic keys, which can be symmetric (same key for encryption and decryption) or asymmetric (public and private keys).
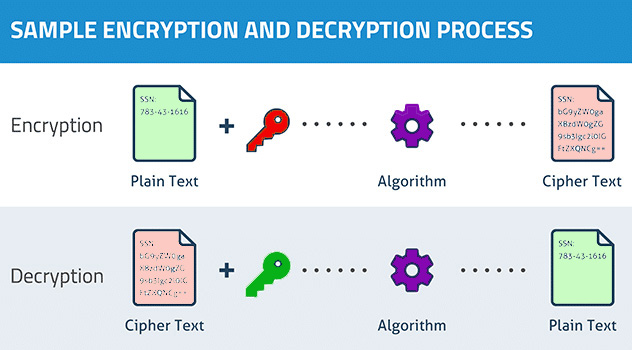
Encryption Algorithms
There are various encryption algorithms available, each with its strengths and weaknesses. Common encryption algorithms include Advanced Encryption Standard (AES), Rivest Cipher (RC4), and Data Encryption Standard (DES). These algorithms use different mathematical operations to transform data into ciphertext and are chosen based on factors like security and speed.
Data Tokenization Explained
What is Data Tokenization?
Data Tokenization, on the other hand, replaces sensitive data with tokens, which are random values that hold no intrinsic value. These tokens are used in place of actual data, and the sensitive information is stored securely in a separate database. Tokenization is commonly used in payment processing systems, protecting credit card information.
The Process of Tokenization
The tokenization process involves capturing data, such as credit card numbers, and sending them to a tokenization system. This system generates a token and associates it with the original data. The token is then used in transactions, and only authorized parties can retrieve the original data from the secure database.
Differences Between Encryption vs. Data Tokenization
Purpose and Usage
Encryption is primarily used to protect data during transmission or when it’s stored, ensuring confidentiality. Data Tokenization, on the other hand, is often used to safeguard sensitive information within databases and systems.
Security Aspects
While both methods enhance security, encryption can be more secure as the data is unreadable without the proper decryption key. In tokenization, the security relies on the protected database and the security of the tokenization system.
Performance and Speed
Encryption can be resource-intensive, potentially affecting system performance, while tokenization is generally faster and more efficient for data retrieval and processing.
Pros and Cons of Encryption vs. Data Tokenization
Advantages of Encryption
- Data Security: Encryption provides a high level of data security, especially when strong encryption algorithms are used. It is suitable for scenarios where the data needs to be protected at all times.
- Versatility: Encryption can be applied to a wide range of use cases, from securing email communications to protecting files and folders. It is highly versatile in its application.
Advantages of Data Tokenization
- Reduced Risk: Data Tokenization reduces the risk associated with data breaches. Even if a breach occurs, the stolen tokens hold no value to malicious actors, as they cannot be used to access sensitive information.
- Ease of Use: Implementing tokenization is often easier and less complex than encryption, making it accessible for various businesses and industries.
Disadvantages of Encryption
- Key Management: Managing encryption keys can be a complex and critical task. If keys are lost or compromised, data can become inaccessible.
- Resource Intensive: Some encryption algorithms demand significant computing resources, potentially slowing down processes, especially in resource-constrained environments.
Disadvantages of Data Tokenization
- Limited Applicability: Tokenization is most effective when dealing with structured data, making it less suitable for unstructured or complex data.
- Token Storage: Storing tokens and the security of the tokenization system are crucial. If the tokenization system is compromised, the data’s security is at risk.
Table Comparison Encryption vs. Data Tokenization
| Aspect | Encryption | Data Tokenization |
|---|---|---|
| Purpose and Usage | Protects data during transmission and storage. | Used to secure sensitive data within databases. |
| Security Aspects | Data is unreadable without the decryption key. | Security relies on the tokenization system and protected database. |
| Performance and Speed | Can be resource-intensive, potentially affecting performance. | Generally faster and more efficient for data retrieval and processing. |
| Data Security | Provides high data security, especially with strong encryption algorithms. | Reduces the risk associated with data breaches. Stolen tokens hold no value. |
| Ease of Use | Versatile, suitable for a wide range of applications. | Easier to implement and less complex, making it accessible to various businesses. |
| Key Management | Complex task, critical for data access. Key loss or compromise can lead to data inaccessibility. | Simplified key management as tokenization relies on the security of the tokenization system. |
| Applicability | Suitable for a wide range of data types and scenarios. | Most effective with structured data, less suitable for unstructured or complex data. |
| Industry Applications | Used in healthcare, finance, government, and various sectors. | Commonly employed in retail, e-commerce, and businesses handling payment data. |
| Combining Methods | Can be combined with Data Tokenization for comprehensive data security. | Can be combined with Encryption for multi-layered data protection. |
When to Use Encryption
- Use Cases: Encryption is ideal for securing sensitive information during transmission, such as online banking transactions, securing confidential emails, and protecting data on portable devices.
- Industry Applications: Encryption is widely used in healthcare, finance, and government sectors where data confidentiality is of utmost importance.
When to Use Data Tokenization
- Use Cases: Data Tokenization is best suited for securing payment information, personal identification numbers, and other structured data within databases.
- Industry Applications: Businesses in the retail and e-commerce industries often use data tokenization to protect customer data and financial information.
When to Choose Encryption vs. Data Tokenization
The choice between Encryption and Data Tokenization depends on the specific security requirements of a given situation. Here are some considerations to help you decide:
- Encryption is Preferred When:
- Data must remain confidential under all circumstances.
- Data is at risk during transmission.
- Regulatory compliance mandates encryption.
- Data Tokenization is Preferred When:
- Data format and structure must be retained.
- Efficiency and speed are a priority.
- Compliance with specific regulations is essential.
Certainly, here’s a table comparing Encryption and Data Tokenization:
Combining Encryption and Data Tokenization
When it comes to data security, a multi-layered approach is often the most effective. By combining encryption and data tokenization, businesses can create a robust defense against data breaches. Encryption can be used for data in transit, while tokenization secures sensitive data at rest, offering comprehensive protection.
Conclusion
In the battle of Encryption vs. Data Tokenization, there is no one-size-fits-all answer. The choice between these methods depends on the specific needs of your organization and the nature of the data you are handling. Understanding the strengths and weaknesses of each approach is crucial in making an informed decision about safeguarding your digital assets.
FAQs:
What is the main purpose of encryption?
The primary purpose of encryption is to secure data by converting it into an unreadable format, ensuring its confidentiality and integrity.
How does data tokenization protect sensitive information?
Data tokenization protects sensitive information by replacing it with random tokens, rendering the original data useless to unauthorized parties.
Can encryption and data tokenization be used together?
Yes, combining encryption and data tokenization can provide enhanced data security by protecting information both in transit and at rest.
Which is more suitable for financial institutions: encryption or data tokenization?
Financial institutions often use a combination of both encryption and data tokenization to secure sensitive customer data comprehensively.
How can I ensure the security of my data with these methods?
Ensuring data security involves proper key management for encryption and robust security measures for data tokenization systems. Regular audits and updates are also essential to maintain data security.

