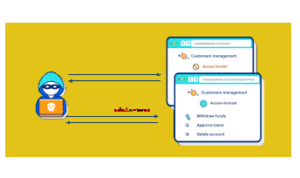
Common Authentication Vulnerabilities – How to Protect Against Them
Discover expert strategies to shield your systems from cyber threats. Learn about the prevalent authentication vulnerabilities and how to safeguard your digital assets effectively.
0 Comments