In this article, you will explore about different common authentication vulnerabilities and how to protect yourself from these attacks. It will be easy to understand.
In today’s digital age, security concerns are paramount. As technology advances, so do the methods of cyber attackers seeking to compromise systems and steal sensitive information. Among the most common types of attacks is the exploitation of authentication vulnerabilities. Discover expert strategies to shield your systems from cyber threats. Learn about the prevalent authentication vulnerabilities and how to safeguard your digital assets effectively. In this article, we will delve into the ten common authentication vulnerabilities that attackers often target and explore ways to mitigate them effectively.
If you intrusted in checing methods of auhtentication in Node.js you can visit: Methods of Authentication and Authorization in Node.js With Code
Table of Contents
- Understanding Authentication Vulnerabilities
- What Are Authentication Vulnerabilities?
- Common Threats to Your Authentication Systems
- Password Guessing and Brute Force Attacks
- Credential Stuffing
- Phishing Attacks
- The Importance of Strong Authentication
- Why Strong Authentication Matters
- Risks of Weak Authentication
- Strengthening Your Digital Defense
- Implementing Two-Factor Authentication (2FA)
- Biometric Authentication
- Top 10 Authentication Vulnerabilities Exposed
- Brute Force Attack
- SQL Injection
- Cross-Site Scripting (XSS)
- Session Fixation
- Man-in-the-Middle (MitM) Attacks
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Insecure Deserialization
- Security Misconfiguration
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
- Unveiling the Critical Weaknesses
- Detailed Analysis of the Top 10 Vulnerabilities
- Protecting Against Attacks: A Comprehensive Approach
- Authentication Best Practices
- Safeguarding Your Digital Identity
- Identity and Access Management (IAM)
- Single Sign-On (SSO)
- Multi-Factor Authentication (MFA) Explained
- How MFA Enhances Security
- Popular MFA Methods
- Securing API Authentication
- OAuth 2.0 and API Tokens
- Rate Limiting and Throttling
- Preventing Account Takeovers
- Suspicious Activity Monitoring
- Automated Account Lockout
- Continuous Monitoring and Incident Response
- Real-Time Threat Detection
- Incident Response Plan Development
Introduction:
Authentication is a fundamental pillar of cybersecurity, serving as the gatekeeper to a system, application, or network. It ensures that only authorized users gain access while keeping malicious actors at bay. However, even this crucial security aspect can have vulnerabilities that attackers exploit. Let’s explore these vulnerabilities in detail and learn how to safeguard against them.
Understanding Authentication Vulnerabilities
Authentication is the cornerstone of digital security. It’s the process by which a user proves their identity to a system or application. However, this crucial aspect of cybersecurity is riddled with vulnerabilities that malicious actors can exploit. Authentication typically involves the use of credentials, such as usernames and passwords, to gain access to a system. Users provide these credentials, and the system verifies their authenticity.
What Are Authentication Vulnerabilities?
Okay, so imagine you have a super secret club, and you need a secret handshake to get in. But sometimes, the bad guys learn the handshake and sneak in! That’s kinda like what happens with computer systems. They have secret handshakes too, and sometimes, bad guys figure them out. 😱
So, Authentication vulnerabilities are weaknesses in the authentication process that cybercriminals can exploit to gain unauthorized access. These vulnerabilities pose a significant threat to your digital assets and sensitive information.
Who Wants to Break In?
Imagine if your treehouse had treasure, and mean squirrels wanted it. They might try to climb up and steal it when you’re not looking. Well, that’s how bad people try to steal your computer secrets, like passwords and stuff. They really want your digital treasure!
Common Threats to Your Authentication Systems
- Password Guessing and Brute Force Attacks
- Cybercriminals attempt to guess passwords or use automated tools to crack them.
- Defend against this by enforcing strong password policies and implementing account lockout mechanisms.
- Credential Stuffing
- Attackers use stolen usernames and passwords from one site to access accounts on other sites where users have reused their credentials.
- Protect against this by educating users not to reuse passwords and implementing 2FA.
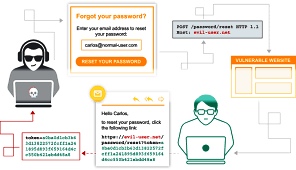
- Phishing Attacks
- Malicious actors trick users into revealing their credentials through deceptive emails or websites.
- Combat phishing with user education and email filtering.
The Importance of Strong Authentication
Why is strong authentication essential?
Why Strong Authentication Matters
- Strong authentication ensures that only authorized users can access systems.
- It helps prevent data breaches and protects sensitive information.
- Regulatory compliance often requires robust authentication measures.
Risks of Weak Authentication
- Weak authentication opens the door to unauthorized access.
- It can lead to identity theft, financial losses, and reputational damage.
- Weak authentication methods are easy targets for cybercriminals.
Improving Your Digital Defense
To bolster your digital defense, consider implementing the following measures:
Implementing Two-Factor Authentication (2FA):
2FA adds an extra layer of security by requiring users to provide two different authentication factors, such as a password and a fingerprint.
Biometric Authentication:
Biometrics, like fingerprint or facial recognition, offer highly secure authentication methods that are difficult for attackers to replicate.
Top 10 Authentication Vulnerabilities Exposed
Now, let’s delve into the top 10 authentication vulnerabilities that threaten your digital security:
- Brute Force Attacks
- SQL Injection
- Cross-Site Scripting (XSS)
- Session Fixation
- Man-in-the-Middle (MitM) Attacks
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Insecure Deserialization
- Security Misconfiguration
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
Following are the Detailed Analysis of the Top 10 Vulnerabilities:
1. Brute Force Attacks:
Imagine someone repeatedly trying to guess your password until they get it right. That’s a brute force attack. Attackers use automated tools to try a vast number of combinations, hoping to crack a weak password.
Mitigation: To defend against brute force attacks:
- Enforce strong password policies with a mix of letters, numbers, and special characters.
- Implement account lockout mechanisms after a certain number of failed login attempts.
- Use CAPTCHA or reCAPTCHA challenges to verify that users are human.
2. SQL Injection:
SQL injection is like a Trojan horse; attackers sneak malicious SQL code into input fields, tricking the application into executing unintended database commands. This can lead to data leakage or even database manipulation.
Mitigation: Protect your application against SQL injection:
- Use parameterized queries or prepared statements to sanitize user inputs.
- Employ an ORM (Object-Relational Mapping) framework that automatically escapes inputs.
- Regularly update and patch your database software to fix known vulnerabilities.
3. Cross-Site Scripting (XSS):
Cross-Site Scripting is an attack where malicious scripts are injected into web pages viewed by other users. This can compromise user data and even lead to session hijacking. To mitigate XSS attacks, input sanitization, and output encoding should be implemented.
Mitigation: Prevent XSS by validating and sanitizing user input and using security headers.
4. Session Fixation:
Session fixation occurs when an attacker sets a user’s session ID, effectively taking control of the user’s session. This allows them to hijack the session and impersonate the user. For example, an attacker might trick a user into clicking a link containing a malicious session ID.
Mitigation: To mitigate this threat, session regeneration and secure session management are crucial. Session regeneration involves changing the session ID after authentication. This ensures that even if an attacker knows an old session ID, it won’t be valid after regeneration. Secure session management includes protecting session data from unauthorized access and destruction of sessions after logout or inactivity.
5. Man-in-the-Middle (MitM) Attacks:
In MitM attacks, cybercriminals intercept communication between users and a system, potentially eavesdropping on sensitive information. For instance, an attacker can position themselves between a user’s device and a public Wi-Fi hotspot to intercept data.
Mitigation: To prevent MitM attacks, use encryption protocols like HTTPS. HTTPS encrypts data transmitted between the user’s browser and the server, making it difficult for attackers to decipher intercepted data. Employing certificate validation ensures that users are communicating with legitimate servers, not impostors.
6. Cross-Site Request Forgery (CSRF):
CSRF attacks trick users into performing unwanted actions without their consent. For example, an attacker could send an email containing a link that, when clicked, makes the user unintentionally change their email password.
Mitigation: Implement anti-CSRF tokens in web applications. These tokens are unique for each user session and must be included in every HTTP request. The server validates the token to ensure the request is legitimate. Additionally, validate requests on the server-side to confirm they originate from an authorized source.
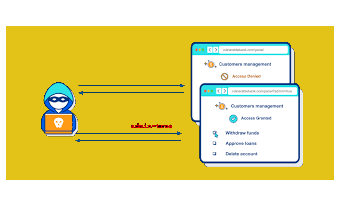
7. Broken Authentication:
Broken authentication vulnerabilities grant attackers unauthorized access to user accounts. For instance, weak password policies or insecure session management can be exploited to gain access to accounts.
Mitigation: To fix broken authentication, enforce strong password policies that require complex passwords. Implement secure session management practices, including strong session ID generation, proper logout procedures, and session timeouts. Regularly review and update authentication mechanisms to stay ahead of evolving threats.
8. Insecure Deserialization:
Attackers exploit insecure deserialization to execute arbitrary code on a system. For example, a maliciously crafted serialized object can trigger code execution when deserialized.
Mitigation: Avoid insecure deserialization by using safe serialization formats and libraries. Restrict deserialization of untrusted or external data sources. Implement input validation and output encoding to prevent malicious data from reaching the deserialization process.
9. Security Misconfiguration:
Security misconfigurations occur when systems are not set up securely. This could include default passwords, overly permissive access controls, or exposed sensitive information.
Mitigation: Regularly audit system configurations to identify and rectify misconfigurations. Follow security best practices and guidelines for hardening systems and applications. Implement the principle of least privilege to limit access to only what is necessary.
10. Using Components with Known Vulnerabilities:
Outdated or vulnerable components, such as libraries or plugins, can be exploited by attackers to compromise a system. For instance, an outdated content management system (CMS) plugin might have a known vulnerability that attackers can exploit.
Mitigation: Keep all software components up to date. Subscribe to security advisories and promptly apply patches or updates when vulnerabilities are discovered. Regularly scan your system for known vulnerabilities using security tools or services.
11. Insufficient Logging and Monitoring:
Inadequate logging and monitoring make it difficult to detect and respond to security incidents. Without proper logs, it’s challenging to track suspicious activities or breaches.
Mitigation: Implement comprehensive logging, capturing both normal and suspicious activities. Set up real-time monitoring to alert security teams to unusual events. Develop an incident response plan to address and mitigate security incidents promptly.
Protecting Against Attacks on Authentication | Safeguard Yourself
Defending against authentication vulnerabilities requires a holistic strategy:
1. Use Strong Password Hashing:
Implement a strong password hashing algorithm like bcrypt to securely store user passwords. This ensures that even if your database is compromised, passwords remain protected.
2. Implement Multi-Factor Authentication (MFA):
Encourage or require users to enable MFA, which adds an extra layer of security by verifying their identity through multiple factors like passwords, biometrics, or security tokens.
3. Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification: something they know (password) and something they have (e.g., a mobile app-generated code).
Implementation: Integrate 2FA libraries like Google Authenticator or use specialized services for 2FA.
4. Session Management:
Manage user sessions securely. Use secure, HTTP-only cookies to store session tokens, and implement session timeout and reauthentication for sensitive actions.
5. Secure Communication:
Always use HTTPS to encrypt data in transit. This prevents eavesdropping and man-in-the-middle attacks.
6. OAuth and OpenID Connect:
If dealing with third-party authentication, consider using OAuth 2.0 and OpenID Connect protocols, which are secure and widely adopted for external authentication.
7. Security Headers: Building a Digital Fort:
Security headers act like the guards at the entrance to your digital fortress. They protect your application from various threats. Set appropriate security headers in your HTTP responses, such as Content Security Policy (CSP), Strict-Transport-Security (HSTS), and X-XSS-Protection, to mitigate common web vulnerabilities.
- Content Security Policy (CSP): Defines which sources of content are considered trusted, preventing cross-site scripting (XSS) attacks.
- HTTP Strict Transport Security (HSTS): Enforces secure connections, reducing the risk of man-in-the-middle attacks.
- X-Content-Type-Options: Prevents browsers from interpreting files as something else (e.g., a malicious script).
8. Rate Limiting: Slowing Down the Attackers
Rate limiting is like controlling the number of people entering a store during a sale to prevent a stampede. It restricts the number of requests from a single source, making it harder for attackers to overwhelm your system.
- Express Rate Limit: A middleware for Node.js and Express.
- API Gateway: If you’re using a microservices architecture.
9. Regular Updates:
Keep your authentication and authorization libraries and dependencies up to date to patch known security vulnerabilities.
10. Security Testing:
Conduct regular security assessments, including penetration testing and code reviews, to identify and address potential security issues.
11. Education and Training:
Ensure that your development team is well-informed about security best practices. Educate users on security awareness, such as recognizing phishing attempts.
12. Fail-Safe Defaults:
Apply secure defaults to your application’s configurations and permissions. Users should explicitly request elevated permissions.
Best Practices for Authentication
Regular Password Changes vs. Strong, Memorable Passwords:
- Encourage users to create strong, unique passwords rather than changing them frequently.
User Education and Training:
- Educate users about the importance of security and the risks of weak authentication.
Identity and Access Management (IAM):
- Implement IAM solutions to manage and control user access effectively.
Single Sign-On (SSO):
- Simplify user access while maintaining security through SSO solutions.
Multi-Factor Authentication (MFA) Explained
How MFA Enhances Security
MFA is like having a fingerprint scanner and a PIN to enter your house. It adds an extra layer of security by requiring multiple forms of verification. MFA adds an extra layer of protection, requiring users to provide multiple forms of authentication.
Popular MFA Methods
- Explore various MFA methods, including SMS codes, biometrics, and hardware tokens.
Implementing Secure Password Policies
Password Complexity Requirements
- Define strong password requirements to prevent easy-to-guess passwords.
Password Storage Best Practices
- Safeguard stored passwords using secure hashing algorithms and encryption.
Continuous Monitoring and Incident Response
Real-Time Threat Detection
- Employ real-time monitoring and threat detection to identify and respond to security incidents promptly.
Incident Response Plan Development
- Develop a comprehensive incident response plan to address security breaches effectively.
Conclusion
In today’s digital landscape, safeguarding your systems against authentication vulnerabilities is paramount. By understanding these vulnerabilities and implementing robust security measures, you can protect your digital assets and data from cyber threats effectively.
FAQs (Frequently Asked Questions)
What is authentication vulnerability?
Authentication vulnerabilities are weaknesses in the authentication process that can be exploited by malicious actors to gain unauthorized access to systems or data.
Why is strong authentication essential?
Strong authentication is crucial because it ensures that only authorized users can access systems, preventing data breaches and protecting sensitive information.
What are some common authentication vulnerabilities?
Common authentication vulnerabilities include SQL injection, cross-site scripting (XSS), session fixation, man-in-the-middle (MitM) attacks, and more.
How can I protect against authentication vulnerabilities?
You can protect against authentication vulnerabilities by implementing strong password policies, multi-factor authentication (MFA), regular security audits, and user education.
What should I do if I suspect an account takeover?
If you suspect an account takeover, immediately lock the affected account and follow your incident response plan to investigate and mitigate the threat.
What are authentication vulnerabilities?
Authentication vulnerabilities are like secret handshakes that bad guys learn to sneak into computer systems.
Why is strong authentication important?
Strong authentication is like a superhero’s defense. It keeps bad guys away from your digital stuff.
What is MFA, and why is it important?
MFA is like having extra locks on your treehouse door. It adds an extra layer of security to your digital stuff.
How can I create strong passwords?
Creating strong passwords is like making secret codes. We’ll show you how to make them super-duper strong!
What should I do if I suspect an attack on my digital accounts?
Be a superhero and keep watch for trouble! If something looks fishy, take action and protect your accounts.